List of topics we’ve previously covered on flespi conf 2023:
In flespi, we’ve embedded security as a fundamental concept to protect your data at every step: during processing, storage, and transmission to third-party platforms. Okay, it's a fundamental approach. But what about a dedicated development team or regional managers to work with data on a specific level? How it’s been organized and whether it’s still super-easy to configure access rights?
You might have already read this brilliant article, so let’s demonstrate it live. In the following video, Aliaksei Shchurko, Chief Gurtam Architect, explains the fundamental approach built-in to provide organized access to the data being consumed in the flespi platform.
The security topic is a complex one… and of incredible importance. Along with the simplicity of API calls being sent, you may easily delete all your devices at once (using a metaphor - it will be like Tanas snapping his fingers).
Surely we have a dedicated backup server to store snapshots and metadata copies. Still, it’s much more useful to follow a set of rules and listen to some advice to organize and manage access rights - to avoid any risks of any security breach or unpredictable human behavior.
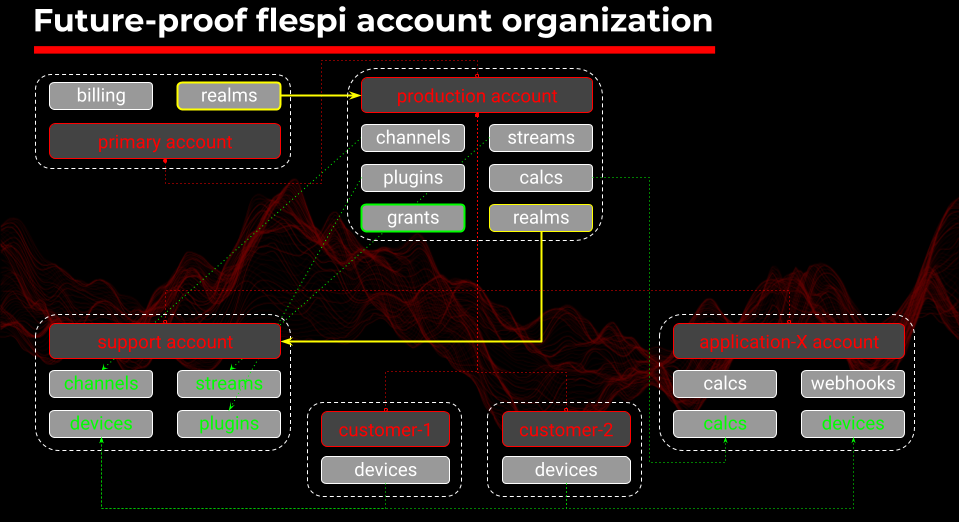
Basically, any flespi account stands for 4 basic terms: tokens, subaccounts, grants, and realms. While tokens can be represented as the keys, and subaccounts - a way to group, isolate, and set limits thus building a hierarchy, the last 2 are experimental and have been introduced recently. Grants help to override this isolation and realms themselves automate subaccounts and token provisioning for authorization.
Experienced users who might have looked through this article are aware of 3 main token types but it wouldn't be superfluous to revise the differences between them (do you know the type of a token that works similar to a firewall). And that’s not all you’re going to learn.
Subaccounts are completely isolated entities still providing a friendly way to assign devices and channels to each of them. Keep in mind that by staying on the upper stair step you observe everything below so building relations between child subaccounts should be done carefully and precisely to keep the data flowing right. Though this solidness still seems logical, but there might be a lack of flexibility, so we implemented an elegant way to improve this.
Grants let you bypass the rigid hierarchy and architect a complex solution that might retrieve data from different subaccounts and do it securely. Realms can be a little tricky to understand but they provide something never done before, they let you deal with a set of users who log in with their own credentials exactly as it’s familiar to any corporate user.
Does it sound intriguing but still hard to imagine it in practice? Here are a few use cases::
share device data with an external party
isolate the client’s data
secure your production account and
provide support team read-only access to flespi
share device in multiple applications
But the topic for discussion was not only to make an account secure but also future-proof. Let's lift the veil of secrecy, this following slide shows it’s not a boast.
In summary, I should mention that there are numerous updates planned for the end of this year, as you might have read in our latest change log. Stay tuned to be among the first to try SSO sign-in and other exciting features coming soon!
Next time, we will be conducting a workshop to explore flespi UI tips & tricks together with our Software Engineer, Jan Bartnitsky, and Frontend Developer, Evgenij Spitsyn.